Secure Innovation
Find out more information about the scheme, and how to apply

Executive Summary
- About
- Funding and Costs
- How to Apply
The scheme bears the majority cost of each Review through a £2,500 grant, with a supplement of £500 from each business. To encourage organisations receiving a security review to progress toward achieving Cyber Essentials certification, a £300 voucher code towards Cyber Essentials will be provided to each participating organisation.
Scheme Framework
The Security Review scheme is funded through a joint initiative between the Department for Business and Trade (DBT), the Department for Science, Innovation and Technology (DSIT), National Protective Security Authority (NPSA), and the National Cyber Security Centre (NCSC). The review will provide a high-level overview of your overall protective security posture -not limited to cyber security. While cyber security remains a critical element, the review will offer a holistic view of security practices by considering the approach to the controls:
Cyber Essentials

Secure Supply Chain and Partnerships

Protective Security Governance

Risk Management

Cyber Security

Security Culture

Incident Management
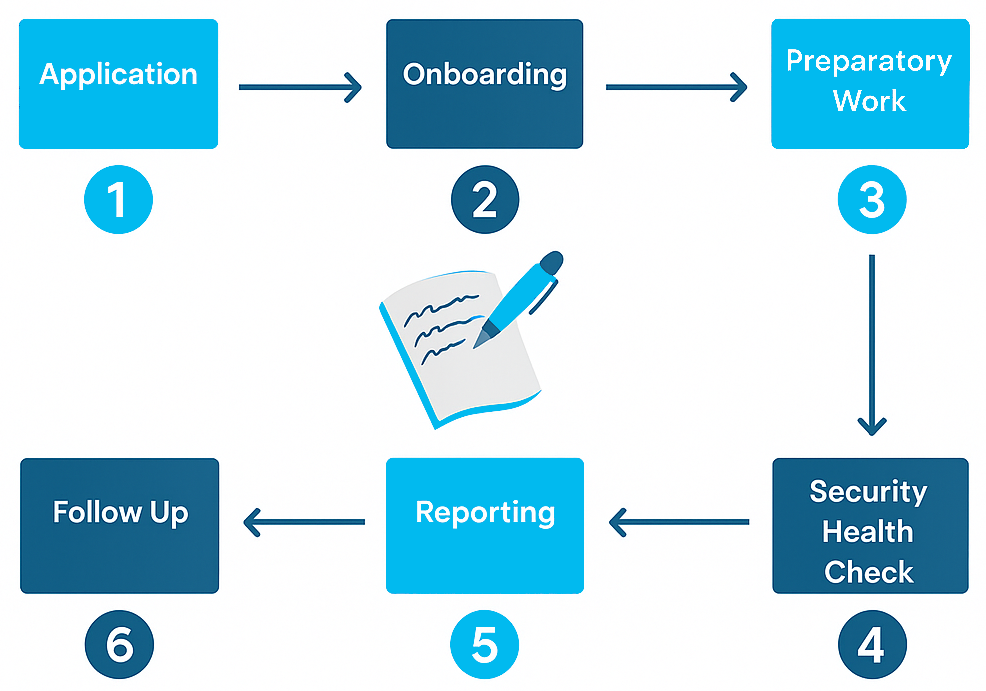
The Path to Secure Innovation
The Secure Innovation Process Consists of 6 Stages:
Secure Innovation Security Reviews is a subsidy scheme with participating companies will contributing £500 (Including VAT); whilst HMG will fund the remaining £2500 (Including VAT). Companies that meet the eligibility criteria and successfully pass the application process will be offered access to the partially funded Secure Innovation Security Review.
- To be accepted onto the scheme, your application must demonstrate that you are both able and willing to dedicate resources, including where necessary financial resources, to effectively implement your protective security strategy.
Your KEYSIGMA consultant will guide you through the formal application process.
Following approval of your application you will need to:
- Formally appoint KEYSIGMA as your security reviewer.
- Agree to the scheme’s terms and conditions.
- Agree to KEYSIGMA’s terms and conditions.
- Pay the £500 contribution towards the assessment.
- Arrange the site visit with your Security Reviewer.
The KEYSIGMA security reviewer will visit your site to review your security arrangements against the Secure Innovation framework. The KEYSIGMA reviewer will use the health check questionnaire to support the engagement and will which covers the following themes:
- Protective Security Governance.
- Security Culture.
- Risk Management.
- Cyber Security.
- Secure Supply Chain and Partnerships.
- Incident Management
It is important to note, that the KEYSIGMA security reviewers delivering the scheme are not be experts in all of these areas and have much more expertise in guidance and implementation of controls relating to Cyber Essentials. The KESYIGMA reviewer will provide guidance on their areas of expertise and will provide guidance aligned with resources from the NPSA and the NCSC for areas outside of our core competencies.
Following the site visit, the KEYSIGMA Security Reviewer will compile a written report that serves as a tailored action plan for your organisation. This report will:
- Summarise the findings from the protective security health check.
- Highlight key areas for improvement.
- Provide practical recommendations. Where appropriate, the report will signpost NPSA and NCSC resources to support you in addressing the identified risks.
Before your chosen Security Reviewer submits the report, it must be signed by you to confirm you are satisfied with its contents. Alternatively, written confirmation of approval via email must be provided as evidence. Copies of the completed reports will be shared with Business West, Innovate UK, NPSA, the NCSC and the DBT and DSIT project teams for monitoring and evaluation purposes. NPSA and the NCSC may dip check a selection of these reports for consistency and quality monitoring.
Follow up Call
Six months after the initial site visit, the KEYSIGMA Security Reviewer will conduct a follow-up call with you to assess progress and identify any ongoing or emerging challenges. During this call, the KEYSIGMA Security Reviewer will complete a second Health Check Questionnaire and produce a 6-Month Follow-Up Report summarising the discussion and any developments since the initial review.
This follow-up is a key component of the overall evaluation of the Secure Innovation Security Reviews scheme. It not only helps measure the impact of the review process but also provides you with a clear understanding of remaining gaps and areas for continued improvement.
Satisfaction Surveys
Following both the site visit and the six-month check-in, you will be contacted to provide feedback on your experience of the Secure Innovation Security Review Scheme. This feedback is a vital part of the programme. By completing the feedback process, you will help us evaluate the scheme’s effectiveness, identify areas for improvement, and assess behavioural change over time.
Step 1 - Application
Contact us to begin the application process and secure your place
Secure Innovation



